DNSSEC News
DNSSEC Operational on XN--H2BRJ9C.
21 May 2013
DNSSEC Operational on GN.
21 May 2013
DNSSEC Operational on YT.
16 May 2013
DNSSEC Operational on XN--ZCKZAH.
16 May 2013
DNSSEC Blog Posts
ICANN to Convene Annual Europe Regional Registry/Registrar Event
March 28, 2011
Planned Changes to IPv4 Reverse DNS Infrastructure
December 15, 2010
An Update on ICANN Security Efforts
November 12, 2010
CEO Remarks on Black Hat / Def Con
August 3, 2010
DNSSEC
To easily identify resources on the Internet, the underlying numerical addresses for these resources are represented by human readable strings. The conversion of these strings to numbers is done by the distributed hierarchical Doman Name System (DNS). Increased sophistication in computing and networking since its design in 1983 have made this "phone book" vulnerable to attacks. Specifically, to the ability of attackers to falsify responses to queries to the DNS thus allowing attackers to redirect end users to Web sites under their own control (for account and password collection) without notice.
In response to these threats, the international standards organization, IETF, developed DNSSEC to cryptographically ensure DNS content cannot be modified from its source without being detected. Once fully deployed, DNSSEC will stop the attacker's ability to redirect users using the DNS. Of particular interest to ISPs and enterprises, DNSSEC will prevent en masse redirection at the DNS resolver (also known as cache poisoning).
DNSSEC works by digitally signing each DNS record so that any tampering of that record can be detected. The digital signatures, and keys used to create them, are distributed just like any other records in the DNS making DNSSEC backward compatible. Keys in each layer in the DNS hierarchy are signed by keys from the preceding layer which effectively vouches for them just like domain names are delegated from one layer to the next. This "chain of trust" is used to validate the digital signatures accompanying DNSSEC protected records to detect changes.

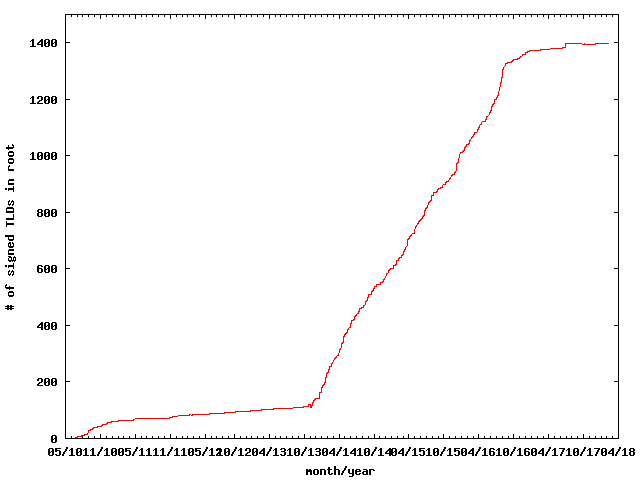
Starting with the discovery of improved DNS exploits in 2008 together with broad multi-stakeholder support, DNSSEC has been deployed at an accelerated pace on many top level domains, the "root", and products. For the public to benefit fully from DNSSEC via the chain of security it establishes from content source to end user, it must be supported by every entity along this chain, e.g., ISPs and domain name owners.
Moving Forward: With the healthy deployment of DNSSEC well on its way and serious efforts to make use of the resulting global PKI to expand the benefits of cryptographic security to the masses, DNSSEC has the potential of becoming a critical link for a wide range of industry applications.
Greater support of DNSSEC by Registrars, ISPs, Registrants, and enterprises will help achieve this potential by building on the international bottom-up, multi-stakeholder DNSSEC infrastructure deployment efforts that have brought us to where we are today. Specifically, to help reap the full benefits of DNSSEC we recommend the following:
- Turn on DNSSEC validation on DNS resolution services.
- Deploy DNSSEC on domain names.
- Raise awareness of the security benefits of DNSSEC and its secure deployment.
Future Applications: Although ancillary to its original purpose, DNSSEC is seen by many Internet veterans as a platform for innovation for a whole new range of Internet security solutions from digital certificates and email to yet to be discovered products. Therefore, gaining experience with DNSSEC may have broader value.
This web page is designed to track activities relating to DNSSEC. For more information on DNSSEC and interest in DNSSEC education and training please contact dnssec@icann.org.