Registry Operator's Proposal
I. GENERAL INFORMATION
D1. Registered name of the company:Eastern Communications Company Limited.
Registered address:No. 80-84,Wensan Road,Hangzhou,Zhejiang, P.R.China.
Tel:+86-571-8865383
Fax:+86-571-8865275
E-mail:webmaster@eastcom.com
D2. No other business location
D3. The registry operator’s type of business entity:Company Limited.
The company is organized under the law of People’s Republic of China.
D4. URL of principal world wide web site: www.eastcom.com.
D5. Dun & Bradstreet D‑U‑N‑S Number:none.
D6. Number of employees: 2340.(by the end of June 2000)
D7. Total revenue (in US dollars) in the last‑ended fiscal year: US$836,603,680.39.
D8. Names and positions of senior managers:
1) COO:Mr.Yuchangming
CFO:Mr.Wangzhongxiong
Vice President:Mr.Zhangzexi
Vice President:Mr.Haoxiaofeng
Vice President:Mr.Chenxuhong
Vice President:Mr.Yuxudong
Vice President & Secretary of the Board:Mr.Shenyuyin
Vice President:Mr.Guojunfeng
2)All relevant managers:
|
Tao Xiongqiang |
Head of R&D Center |
|
Li jingjing |
Head of President's Office |
|
Zhang liangzhong |
Head of Finance Division |
|
Xu xiaoli |
Assistant of President & Head of Human Resource Divison |
|
Gu guoying |
Chief of the Business Delegates& Head of Trading Division |
|
Mao jieming |
Head of Technology Quality Division |
|
Gu kunming |
Head of Corporate Planning and Management Division |
|
Shen zhineng |
Head of MCIG (Mobile Cellular Infrastructure Group) |
|
Lu lixin |
Head of Transmission Equipment Division |
|
Wang jianzhong |
Head of Electronic Equipment Division |
|
Chen deming |
Head of Machining Division |
|
Sun yihao |
Head of Power Equipment Division |
3)Persons or entities owning five percent or more of registry operator(up to 20th Sept,2000)
Zhejiang Eastern Communications Group Co.,Ltd.:51.59%
Zhejiang Eastcom Holding Co.,Ltd.:5.73%
D9.Contact information:
1) Name: Chen Jiangping
Tel: +86 571 8865383
Fax: +86 571 8865275
2) Name: Yao Qing
Tel: +86 571 8865020
D10. No subcontractors
II. BUSINESS CAPABILITIES AND PLAN
D11. The second section of the Registry Operator's Proposal (after the "General Information" section) is a description of the registry operator's Business Capabilities and Plan. This section must include a comprehensive, professional‑quality business plan that provides detailed, verified business and financial information about the registry operator. The topics listed below are representative of the type of subjects that will be covered in the Business Capabilities and Plan section of the Registry Operator's Proposal.
D13. The Business Capabilities and Plan:
D13.1.1 Company information:
Date of formation: 1st Aug,1996
Legal status:Lawfully existing,under legal management,with no momentous lawsuit or disputes.
Primary location:No. 80-84,Wensan Road, Hangzhou, Zhejiang, P. R.China
Size of staff:2340
Formal alliances:MOTOROLA、WINCOR NIXDORF、TEXAS INSTRUMENTS、ARTHURANDERSEN、SIEMENS、QUALTUMM、MICROSOFT
Ownership structure(up to 20th Sept,2000):
|
Name of shareholder |
Number of shares |
percentage |
|
Zhejiang Eastern Communications Group Co.,Ltd. |
324,000,000 |
51.59% |
|
Zhejiang Eastcom Holding Co.,Ltd. |
36,000,000 |
5.73% |
|
A Shares |
118,000,000 |
18.79% |
|
B Shares |
150,000,000 |
23.89% |
|
Total |
628,000,000 |
100% |
D13.1.2. Current business operations.
Core capabilities:offer the total solution of mobile network
Services offered:mobile network design, develop, produce& provide mobile system & terminal products, system work supervising & guidance,network optimize,technology support & service, domain name registration & correlation internet service.
Products offered:Cellular Mobile System Equipments, Mobile Telephone, Mobile Network Increment Software, Mobile Network Specialty Service, Light communications Equipments, Laser Typesetter Equipments, Finance Electron Network Products, Information systems Network Products.
Duration of provision of services and products:1990(From its predecessor)
D13.1.3. Past business operations/entity history.
As the predecessor of Zhejiang Eastern Communications Co., Ltd., Zhejiang Posts and Telecommunications Equipment Factory was grew out of Equipment Supply Office of Zhejiang Posts and Telecommunications Bureau in August, 1958. At that time, the factory was principally engaged in the R&D of carrier phone terminal, series equipment for teleconference, dispatcher equipment with super-high frequency and many telecommunications products.
In July 1962, the factory name was changed into Hangzhou Posts and Telecommunications Equipment Factory and it was administrated by the Ministry of Posts and Telecommunications(MPT). In 1970, the General Office of Telecommunications took the place of MPT. Hangzhou Posts and Telecommunications Equipment Factory was governed by the General Office of Telecommunications, it was named by code 522. In June 1981, this code name(522) was changed into Hangzhou Telecommunications Equipment Factory of MPT.
In July 1994, Hangzhou Eastern Communications Chuangye Company was established. As the wholly-owned subsidiary company of Hangzhou Telecommunications Equipment Factory, it was concentrated with many departments which were in charge of manufacturing and sales of mobile communications equipment. It was registered in Hangzhou high-tech industry developed region.
Hangzhou Communications Co., Ltd. was established on 18th April, 1996 and it succeeded to the whole assets and liability of the former Hangzhou Telecommunications Equipment Factory.
On the base of Hangzhou Eastern Communications Chuangye Company, Eastern Communications Co., Ltd.(Eastcom) was established by IPO on 21st May,1996.
B and A shares of Eastcom were listed for transaction at Shanghai Securities Exchange(SSE) on 9th August and 26th November, 1996 respectively.
D13.1.4. Related experience and activities: EASTCOM is one of ICANN accredited registrar and has full experience in Domain name registration and relevant activities.
D13.1.5. Mission. The registry operator's mission and how it relates to expansion into the registry operation field.
We have got ISP license from our government and have accredited by ICANN as a domain name registrar. It is a strategic movement that Eastcom is going to INTERNET fields.
D13.1.6. Management.
Mr. Shijixing, chairman of the Board & CEO,aged 58, senior engineer, graduated from Beijing Posts and Telecommunications University in 1967. Mr. Shi is the vice chairman of the Board of Eastern Communications Group Co., Ltd., the deputy President. Mr. Shi was the head of the product research department and the director of the new product institute of HCCL. He was the head of the factory in 1988. Mr. Shi has won many awards, including the 1994 PRC National Excellent Enterpreneur (Golden Ball Award) and the Labour Model of Zhe Jiang Provience. He is recognized as an expert with outstanding contribution to the state and is entitled to a special subsidy from the state.
Ms. Wang Lihua, vice chairwoman of the board,aged 51, senior engineer, graduated from Zhe Jiang University in 1976. She is now the vice chairwoman and the deputy President of Eastern Communications Group Co., Ltd., She was the head of the organization department of HCCL.
Ms. Zeng Yu, director of the board,aged 56, senior accountant, is the President of the finance department of China PTIC Information Industry Corporation. Ms Zeng has held various positions with PTIC including assistant accountants, accountant and a deputy manager in business and finance department.
Mr. Xie Yupu, aged 58, senior engineer, is the vice-chairman of Eastern communications Co., Ltd and technical advisor. Mr. Xie graduated from Beijing Posts and Telecommunications University in 1968. Mr. Xie held a number of positions at HCEF, including director of New Products Research Institute, deputy chief engineer and deputy director. Mr. Xie has been awarded the title of Expert with Outstanding Contribution to the State, which award entitles him to receive a special subsidy from the State.
Mr. Yu Changming, director of the board & COO,aged 51, senior engineer, graduated from Zhe Jiang University in 1973.Mr. Yu held various positions at HCEF, including head of the production department, assistant to the factory director, head of the director’s office, deputy director and President of the MCIG division.
Mr. Wang Zhongxiong, director of the board & CFO,aged 47, senior economist. he received a university education. Mr. Wang held various positions at HCCL, including secretary to the factory director, head of the finance department and deputy chief accountant.
Mr. Zhang Zexi, aged 45, senior engineer, graduated from college, is the deputy President of Eastern Communications Co., Ltd. He was the head of production department, sales department of HCEF.
Ms. Ni Shouping, director of the board ,aged 36, graduated from college, certified accountant, senior accountant. Ms Ni is the general accountant of Eastern communications Group Co., Ltd. She was the assistant manager of finance department of HCCL and the manager of finance department of Eastern Communications Co., Ltd.
Mr. Pan Yunhe, independent director of the board ,aged 54, graduated from shanghai Tongji University majored in architecture in 1970 and graduated from Zhe Jiang University with Master Degree, majored in computer. Mr. Pan is a computer specialist and academician. He is the president of Zhe Jiang University and graduate school. Since 1990, he has been the director of research institute, dean of computer department and vice president of Zhe Jiang University.
Mr. Gu Jun, independent director of the board ,aged 44, is the chief scientist of China Electrical Information Industry Group Corporation. Mr. Gu graduated from China Science and Technology University majored in electronic engineering in 1982. He got the PhD of computer from Utah University in 1989. He is now the computer professor of Hong Kong Science and Technology University and China Science and Technology University.
Mr. Lu Guanqiu, independent director of the board ,aged 55, senior economist, is the chairman of Zhe Jiang entrepreneur association and Chairman of the Board of Wanxiang Group. The group was established in 1969 and total assets amounted to RMB 5 billion. He was awarded the title of excellent entrepreneur and model worker.
Mr. Shen Yuyin, aged 32, engineer, graduated from Shanghai Tongji University, is the deputy President & secretary to the Board of Directors. He served as an assistant to the director of a branch.
Mr.Hao Xiaofeng, aged 50,master degree,senior engineer,is the deputy President.Mr. Hao held various at HCEF,including head of the information office,head of the technology import office,President of th MCIG division and Trading Division and President of th MCSG Division.
Mr.Chen Xuhong, aged 57, senior engineer, is the deputy President.Mr.Chen has a Bachelor of Science from TsingHua University. He held various positions at HCEF, including head of New Products Research Institute, deputy chief engineer,chief engineer and President of the MCSG Division.Mr. Chen was awarded the title of Expert with Outstanding Contribution to the state,which award entitles him to receive a special subsidy from the State.
Mr.Yu Xudong,aged 46,senior engineer,is the deputy President.He received a university education.Mr. Yu was the deputy director of the Switching Branch of HCEF,President of SPC division,standing vice president of the Great Dragon Telecommunications Equipment Co.,Ltd., president of the Marketing Group of Eastern Communications Group Co.,Ltd.
Mr. Guo Junfeng, aged 31, engineer, graduated from Shanghai Science and technology University with bachelor degree in 1990 and graduated from Zhe Jiang University with MBA in 1998. He is the deputy President & the President of Terminal Communications Products Sales and Marketing Group. He served as assistant manager of R&D Center and the deputy President of Subscriber Division.
D13.1.7. Staff/employees.
The number of current staff in the company is 2340,73% of whom have bachelor’s degree or above, and more than 140 have master’s or doctor’s degree. Among these staff, 33% are scientific research personnel,32% are marketing & service personnel, 25% work as manufacture personnel,and the other(10%) are manage personnel.
D13.1.8. Commercial general liability insurance. Address/include amount of insurance policy, provider of policy, plans for obtaining additional insurance.
Total value of the insurance is RMB 1.2 Billion (about US$144.6 Million).
Details see Annex D_6.
D13.2. Business plan for the proposed registry operations. This section should present a comprehensive business plan for the proposed registry operations. In addition to providing basic information concerning the viability of the proposed operations, this section offers the registry operator an opportunity to demonstrate that it has carefully analyzed the financial and operational aspects of the proposal. At a minimum, factors that should be addressed are:
D13.2.1. Services to be provided. A full description of the registry services to be provided.
Domain registration, renewal , transfer, modification, etc., the same as NSI.
Whois service, the same as NSI.
Other services detailed in ICANN-NSI agreement.
D13.2.2. Revenue model. A full description of the revenue model, including rates to be charged for various services.
We suppose EASTCOM will adopt the same revenue model as NSI at the beginning of its operation.
Only register service is considered chargeable, and the yearly fee for per new or extend domain name registration is US$6.00.
D13.2.3. Market. Market definition, size, demand, accessibility.
All internet users are our potential customers. The market size is 170 million or so in 1999 and the market is booming and the figure of customers will be expected to 600 million by the end of 2001, which shows a great market in the area of internet.
Among this market size more than 5% is willing to obtain its own domain name in the new TLD, which will consist of the market demand of domain name.
Among the market demand more than 10% is willing to register its own domain name in the new TLD.
D13.2.4. Marketing plan. Advertising, publicity, promotion strategy, advertisement development strategy, relationship with advertising firm. Use of registrars and other marketing channels.
Eastcom has good relationship with some famous advertising firm, consulting firm, website, and other media unit, which will become Eastcom’s publicity channels. Eastcom also has the throughout sales network to promote, distribute, sale its products and provides the relevant services. All the above-mentioned publicity channels and network will consist of the main marketing channels of new TLD. Besides, Eastcom will designate registrars as the other main marketing channels.
D13.2.5. Estimated demand for registry services in the new TLD. Projected total demand for registry services in the TLD, effect of projected registration fees, competition. Please provide estimates for at least 10%, 50%, and 90% confidence levels.
The total demand for registry services in .shop TLD will reach about 10 million, if the registration fees keep the same level as in .com, and it will cause limited competition in the field of registration. We have full confidence of this.
As to the other TLD strings we suppose in this application, the total registration volume may be less, but if some competitive price policy be adopted , they certainly have their own value. One thing is doubtless , they all will lead to the same result: bring some proper competition in the field, and this will help the DNS grow in a more reasonable way.
D13.2.6. Resources required to meet demand. Provide a detailed estimate of all resources (financial, technical, staff, physical plant, customer service, etc.) required to meet the estimated demands, using at least the 10%, 50%, and 90% confidence levels.
Details see Annex D_1.
D13.2.7. Plans for acquiring necessary systems and facilities. Describe plans for acquiring all necessary systems and facilities for providing the proposed services at each estimated demand level. Provide details as to the scope, cost, and vendor for any significant planned outsourcing.
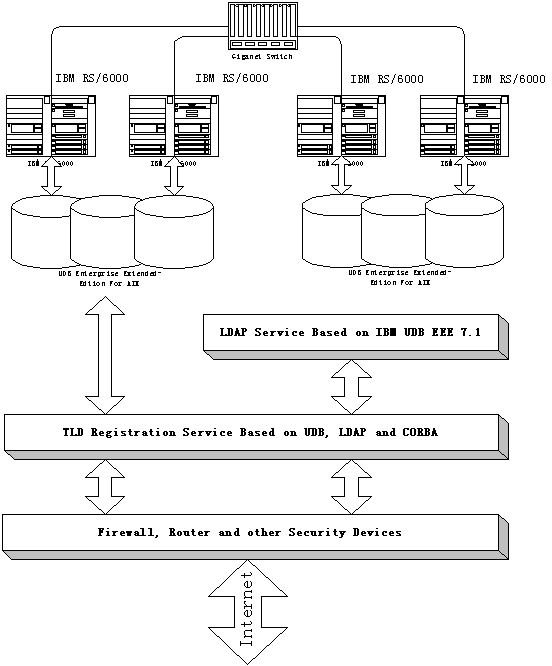
It is most likely that the demand peak of registration will occur at the beginning, so we should take this situation into consideration when we choose network equipment and database software. Using application software with multi-layer structure to provide service take the advantage of better scaleable, and this can be achieved easily whenever it’s necessary.
|
Product |
Vender |
Price |
Quantity |
Sum |
Remark |
|
UDB Enterprise Extended Edition for AIX |
IBM |
US$250,000 |
4 |
US$1,000,000 |
One set per site |
|
RS/6000 Cluster |
IBM |
US$500,000 |
4 |
US$2,000,000 |
Database Server |
|
PC Server |
IBM |
US$50,000 |
50 |
US$2,500,000 |
Including Application Server and Backup Server |
|
Backup Software and Hardware |
IBM & CA |
US$100,000 |
4 |
US$400,000 |
Database Backup |
|
Registry Software |
EASTCOM |
US$500,000 |
1 |
US$500,000 |
|
|
Network management & relevant software |
Cisco & CheckPoint |
US$200,000 |
4 |
US$800,000 |
|
|
Network Equipment |
Cisco |
US$250,000 |
4 |
US$100,000 |
|
|
Sub total |
|
|
|
US$8,200,000 |
|
|
Standby |
|
|
|
US$300,000 |
For other equipment |
|
Total |
|
|
|
US$8,500,000 |
|
Every 10,000,000 additional registrations needs following investment:
|
Product |
Vender |
Price |
Quantity |
Sum |
Remark |
|
RS/6000 |
IBM |
US$200,000 |
4 |
US$800,000 |
|
|
PC Server |
IBM |
US$50,000 |
10 |
US$500,000 |
Provide Whois service |
|
Total |
|
|
|
US$1,300,000 |
|
Every 10 additional registrars needs following investment:
|
Product |
Vender |
Price |
Quantity |
Sum |
Remark |
|
PC Server |
IBM |
US$50,000 |
6 |
US$300,000 |
Application Server |
|
UDB License |
IBM |
US$20,000 |
10 |
US$200,000 |
Client access license |
|
Total |
|
|
|
US$50,000 |
|
D13.2.8. Staff size/expansion capability. Plans for obtaining the necessary staff resources, capacity for expansion, hiring policy, employee training, space for additional staff, staffing levels needed for provision of expanded technical, support, escrow, and registry services.
More than 300 professional people will be employed to execute this project. The total staff will reach 500 in the next two or three years. In China more and more people pay more attention to the IT industry which provides enough human resources. Eastcom will provide competitive salary, option stock and long-term training to employ enough technical staffs. Eastcom is now constructing Eastcom City with the area of more than 300,000 square meters of which will be designated to the special space for additional staff.
D13.2.9. Availability of additional management personnel. How will management needs be filled?
Eastcom will designate one VP who directly report to CEO, in charge of this project and such project has the priority to obtain all resources such as financial, staff, technical, physical demands, etc.. During the next several years, such project will be developed as the main business of Eastcom.
D13.2.10. Term of registry agreement. State assumptions regarding the term of any registry agreement with ICANN or the sponsoring organization. Note that the .com/.net/.org registry agreement has a basic term of four years.
5 year.
D13.2.11. Expected costs associated with the operation of the proposed registry. Please break down the total estimated operational costs by the sources of the costs for each estimated demand level. Be sure to consider the TLD's share of ICANN's cost recovery needs. (See <>.)
Details see Annex D_1.
D13.2.12. Expected revenue associated with the operation of the proposed registry. Please show how expected revenue is computed at each estimated demand level.
Details see Annex D_1 .
D13.2.13. Capital requirements. Quantify capital requirements in amount and timing and describe how the capital will be obtained. Specify in detail all sources of capital and the cost of that capital (interest, etc.). Evidence of firm commitment of projected capital needs will substantially increase the credibility of the registry operator's proposal.
Eastcom
will invest US$ 10,000,000 to 20,000,000 in the next year. Eastcom have already
prepared the necessary capital.
D13.2.14. Business risks and opportunities. Describe upside and downside contingencies you have considered and discuss your plans for addressing them.
The registration quantity is main business risk and opportunity. If the registration quantity can’t reach the expected volume, Eastcom will keep on promoting the project.
D13.2.15. Registry failure provisions. Please describe in detail your plans for dealing with the possibility of registry failure.
Although EASTCOM will use all the possible technical method to avoid such failure, we know for sure the commercial preparation for such occasional failure is necessary. We will minimize the loss from such a failure by commercial insurance and third-party guarantee.
Details see D15.2.12.
D13.3. Pro‑forma financial projections. Please provide detailed pro‑forma financial projections, consistent with your business plan, for the demand scenarios that you estimate under item D13.2.5. The pro‑formas should show revenue and expense estimates broken down by detailed categories and should be broken down into periods no longer than quarterly.
We have made a 5-year financial project of this registry operation. And you can get all the detailed information from Annex D_1.
D13.4. Supporting documentation. The following documentation should be provided in support of the Business Capabilities and Plan section:
D13.4.1. Registry operator's organizational documents. Documents of incorporation (or similar documents).
Details see Annex D_2
D13.4.2. References. A list of significant trade and credit references.
Details see Annex D_3
D13.4.3. Annual report. The registry operator's most recent annual financial report (or similar document). Audited financials are preferred.
Details see Annex D_4
D13.4.4. Proof of capital. Provide evidence of existing capital or firm commitments of capital. Demonstrated access to necessary capital will be carefully scrutinized.
Details see Annex D_5
D13.4.5. Proof of insurance. Please provide proof of the insurance described in item D13.1.8.
Details see Annex D_6
III. TECHNICAL CAPABILITIES AND PLAN
D14. The third section of the Registry Operator's Proposal is a description of the registry operator's Technical Capabilities and Plan. This section must include a comprehensive, professional‑quality technical plan that provides a detailed description of the registry operator's current technical capabilities as well as a full description of the operator's proposed technical solution for establishing and operating all aspects of the registry. The technical plan will require detailed, specific information regarding the technical capabilities of the proposed registry. The topics listed below are representative of the type of subjects that will be covered in the Technical Capabilities and Plan section of the Registry Operator's Proposal.
[ICANN will extensively review and analyze this section of the Registry Operator's Proposal. The content, clarity, and professionalism of this section will be important factors in ICANN's evaluation of applications. We strongly recommend that those who are planning to apply secure professional assistance from engineers and/or other technical consultants to aid in the formulation of the technical plan and the preparation of the Technical Capabilities and Plan section of the Registry Operator's Proposal.]
D15. The Technical Capabilities and Plan section should consist of at least the following:
D15.1. Detailed description of the registry operator's technical capabilities. This should provide a detailed description of the registry operator's technical capabilities, including information about key technical personnel (qualifications and experience), size of technical workforce, and access to systems development tools. It should also describe the registry operator's significant past achievements. This description offers the registry operator an opportunity to demonstrate the extent of its technical expertise in activities relevant to the operation of the proposed registry.
technical capabilities of Eastcom, including:
1) key technical personnel (qualifications and experience),
|
name |
Degree |
Graduate academy |
Major |
Project engaged Now |
|
Tao Xiongqiang |
Doctor |
Zhejiang university |
Information and Electricity |
Director of R&D Center |
|
Wu Yue |
Doctor |
Zhejiang university |
Biomedical Engineering and Instruments |
ATM B-band Switch Platform |
|
Yang Haibo |
Doctor |
Zhejiang university |
Communication and Information System |
ATM B-band Switch Platform |
|
Ye Jun |
Doctor |
Zhejiang university |
Measurement and test Techniques and Instruments |
Collectivity design of SDH transmission equipment |
|
Wang Chao |
Doctor |
Shanghai Tongji University |
Image dispose and Pattern Recognition |
CDMA switch |
|
Cheng Xiaoxiong |
Doctor |
Shanghai Jiaotong university |
Image Communication |
CDMA switch |
|
Zhang Zheliang |
Doctor |
Zhejiang university |
Biomedical Engineering and Instruments |
Design main control software of CDMA switch |
|
Qian Guoliang |
Doctor |
Harbin institute of technology |
Computer application |
In charge of SDH transmission equipment and access network equipment |
|
Luo jianjun |
Doctor |
Zhejiang university |
semiconductor |
ASIC design |
|
Li Wenhua |
Doctor |
East-south university |
Communication and Signal Processing |
ATM B-band Switch Platform |
|
Yang yongkang |
Master |
Shanghai Jiaotong university |
Communication and Electric System |
Senior engineer |
|
Kang jian |
Master |
China spin university |
Automation |
In charge of ATM B-band Switch Platform |
|
Ding ta |
Master |
Zhejiang university |
Communication and Electric System |
SDH transmission equipment |
|
Yao junwu |
Master |
Xian Jiaotong university |
Applied Mathematics |
Design main control software (Signaling and protocol) of CDMA switch |
|
Cheng yuxin |
Master |
Zhejiang university |
Microwave technology |
Design Network Management of SDH transmission equipment |
|
Huang chaoyang |
Master |
Zhejiang university |
Machine |
Product Design |
|
Chen chi |
Master |
Zhejiang university |
Test Techniques |
Design main control software of SDH transmission equipment and access network equipment |
|
Cao yu |
Master |
Zhejiang university |
Optical instrument |
SDH transmission equipment |
|
Za hongmei |
Master |
Zhejiang university |
Detect |
Design MSC main control software CDMA switch |
|
Guo jianping |
Master |
Zhejiang university |
Precision instrument |
SDH transmission equipment and access network equipment |
Name |
Degree |
Graduated academy |
speciality |
post |
|
Cao yu |
Bachelor |
Shanghai teachers unversity |
Computer application |
Software designer |
|
Yao qing |
Bachelor |
Fudan university |
Autocontrol |
Senior systems engineer |
|
Jin hua |
Bachelor |
University of electronic science and technology of china |
Compunication |
Senior network engineer |
|
Zheng jian zhong |
Bachelor |
Lanzhou university |
Computer |
Senior Software engineer |
|
Miao yajun |
|
Fudan university |
Administrative Management |
Web designer |
|
Cai jun feng |
|
Zhejiang institute of electronic technology |
Computer application |
network engineer |
|
Zhang bing |
Bachelor |
Zhejiang university |
Communication and electronic |
systems engineer |
|
Wu fei |
Bachelor |
Xi an highway university |
Computer application |
Senior Software engineer |
|
Chen jiangping |
Master |
Zhejiang university |
MBA/computer |
Department director |
|
Cen kai |
Bachelor |
East China University of Science and Technology |
Polymer science & Engineering |
Senior engineer |
|
Weng ting |
Bachelor |
|
Wireless communication |
Senior Software engineer |
|
Jiang yongjun |
Bachelor |
Hangzhou institute of electronic technology |
Electronic application |
Senior Software engineer |
|
Kong tianmiao |
Master |
Zheng Jiang University of Technology |
Mechanization Engineering |
Senior Software engineer |
|
Lin xiaoyue |
|
Zhejiang radio and television university |
Engineering Electrical |
Software engineer and system engineer |
|
Wan zhaobing |
Bachelor |
Hangzhou university of commerce |
Economy and communication |
Network engineer |
|
Chen huapeng |
Master |
Zhejiang University |
Computer science |
Senior Software engineer |
|
Gao liqiang |
Bachelor |
Hangzhou institute of electronic technology |
Computer |
system engineer |
D15.2. Technical plan for the proposed registry operations.