The information
contained in this document is intended for Baltimore Technologies personnel,
those persons named as recipients or those persons nominated in the circulation
list.
It may contain
privileged and confidential information and if you are not the intended
recipient you must not copy, distribute or take any action in reliance on
it. If you have received this document
in error, please notify the author immediately by reverse charge telephone call
and return the original to the sender by mail.
You will be reimbursed for postage.
Contact:
Global
Hosting Services
Needham
Heights
Massachusetts
USA 02494
Tel:
+1 781 455 3846
Fax: +1 781 455
4082
|
|
|
Signature
Director Business Development
|
|
AMENDMENT
|
EFFECTED
|
|
No.
|
DATE:
|
NOTES
|
NAME
|
|
00/000
|
26SEP2000
|
DOCUMENT
CREATED
|
W.T.OSBORNE
|
As new standards emerge, or policy matters
are identified for improvement, this policy document will be amended.
The
responsibility for amending this document rests with the Director, GHS Business
Development. The naming convention for
amendment notices shall be:
YY indicating the year the amendment
was issued;
XXX where XXX represents a
sequential number that begins with 000.
Table
of Contents
TITLE PAGE......................................................................................................................................................................................... 3
Director – Business Development........................................................................................................................................... 3
AMENDMENTS................................................................................................................................................................................... 4
Amendment
table.................................................................................................................................................................. 4
Amendment
procedure....................................................................................................................................................... 4
INTRODUCTION AND OVERVIEW............................................................................................................................................... 5
Purpose
of paper...................................................................................................................................................................... 5
Baltimore
COE........................................................................................................................................................................... 5
Defence
in Depth...................................................................................................................................................................... 5
Needham COE - Overview..................................................................................................................................................... 6
Security controls........................................................................................................................................................................ 6
Documentation........................................................................................................................................................................... 7
Dublin
COE.................................................................................................................................................................................... 7
The purpose of this document is to provide
a statement regarding the security facilities in place in Baltimore’s Hosting
facilities. In particular this document highlights the facility standards for
the Needham COE and the Dublin COE.
Baltimore presently operate four Centres Of
Hosting Excellence (COE) in the following locations:
|
·
Dublin, Republic of Ireland
|
·
Needham, USA
|
|
·
Sydney, Australia
|
·
Saporro, Japan
|
The
overriding principle for securing any Public key infrastructure (PKI) Hosting
facility is the conceptualisation and practice of “Defence In Depth”.
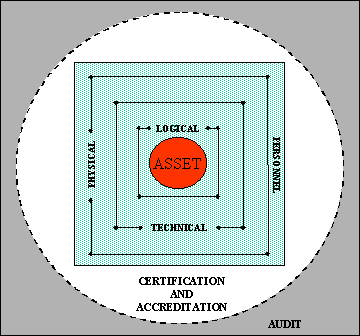 Figure 1 Defence in Depth
Figure 1 Defence in Depth
The Defence
in Depth principle relies upon mutual redundant and supportive layers of
protective security measures.
Figure 1.0 below shows the asset to be
protected existing at the centre of the diagram. Surrounding the asset are layers of protection including:
|
·
Logical
|
·
Technical
|
|
·
Physical
|
·
Certification & Accreditation
|
|
·
Audit
|
·
Personnel Vetting
|
The Needham COE is located in 77 A Street
Needham Heights, Massachusetts USA.
Approximately 4000 square feet of floor space are given over to the
hosting of the Public Key Infrastructures (PKI).
Physical
protections are implemented through the use of
guard service (7 x 24) alarm systems, several layers of physical barriers,
combination locks, restricted key sets and the separation of infrastructure
elements.
Logical
protections include consistent platform
construction, use of system hardening for operating systems and databases,
active audit of system logs, use of certified technologies, (ITSEC, FIPS), and
finally the use of dual firewalls including provisioning of demilitarised Zones
(DMZ) within the logical configurations.
Technical
Security Controls include the provision of
protections for Private keys, PSE files and the control of both Public keys and
Certificates.
Personnel
vetting is a three part process consisting of the
high standard recruiting including positive vetting of claims made, and a
stringent interview, this is followed by the completion of an independent third
party review of the employees background including criminal record checks. Finally each employee is required to enter
into confidentiality agreements that protect the privacy and confidentiality of
customer data.
Certified
technologies include the use of Baltimore’s own
Information Technology Security Evaluation Criteria (ITSEC) E3 Certified PKI
technology. This is complimented with
the use of certified technologies such as the Sureware Keeper, one of only
three products to have completed an evaluation under the USA Federal
information processing Standard (FIPS) level One –4 schema.
Audits
include independent review by third parties to
thoroughly review the operation of Baltimore COE’s. In the case of the Needham COE, Baltimore has completed several
reviews including:
·
SAS 70 Level 1 and 2 Accreditation
·
SET Accreditation
·
Independent review by American
Express, Mastercard and VISA
In addition to these, further evaluation
are planned for accreditation’s including:
·
Identrus Delta
·
AICPA?CPA Guidelines for CA Audit
Needham COE ahs a well developed set of
policy and practice documents that apply to the Baltimore Certificate
management system products and services.
As Needham COE move forward with the hosting of Baltimore UniCERT
technologies a new set of documentation is being adopted. On completion of the transition process, it
is expected that all Baltimore COE will operate under a single set of
operational doctrine.
Dublin COE is located in the Baltimore
corporate headquarters building in Parkgate street Dublin. The newest of our four facilities, this COE
complies with all of the requirements identified and discussed in the
discussion on the Needham facility. The
primary exception is in the use of video or closed circuit camera systems.
In accordance with standard COE policy and
structure, redundancy of systems is a core requirement for operational
excellence. The Dublin COE features
redundant power and communications facilities, including minimum configuration
supporting T1 telecommunications with differentiation between communications
technologies. Also supported are
separate service providers to minimise service disruptions and maintain
competitive pricing.
Finally, UPS systems are maintained
throughout the facilities, and serve to maintain power supplies in the event of
failure and also to ensure that power conditioning is maintained.

